Everything posted by Sandeep B.
-
2FA for CWP
I understand the frustration, please mail your comment to the head developer here `info@centos-webpanel.com` I already notified the developers multiple times but the fact is they are busy with more important fixes in cwp and 2fa fix is in there list.
-
CWP and PageSpeed Module?
you should use it with Apache only as latest nginx is not compatible with pagespeed better to use script side js, css optimizer/plugin/module it will give you best performance
-
Problem in install SSL Wildcard CWP
Seems correct
-
Problem in install SSL Wildcard CWP
And regarding new line error Add a new line and save the dns record. Simply hit enter button at the end of the file to give new line.
-
Problem in install SSL Wildcard CWP
Seems you've added the A record for acme remove that it is completely unnecessary. restart the dns server it will get started.
-
Problem in install SSL Wildcard CWP
In this situation remove the domain name from the txt name record so it will look like: _acme-challenge After restart the dns server. Also you don't need to add A record for the _acme-challenge
-
Problem in install SSL Wildcard CWP
Yes few minutes after restarting the dns server.
-
Problem in install SSL Wildcard CWP
After _acme-challenge.clovstore.com add dot It should be : _acme-challenge.clovstore.com. Then restart the bind/named dns server
-
Problem in install SSL Wildcard CWP
Hi can you send the screenshot of the dns in raw file edit format?
-
How to Reset root password in MariaDB 11.xx/10.xx and Mysql 8.0
In this tutorial I’ll provide you the steps to reset root password for MySQL 8.0 and MariaDB 10.4/10.xx/11.xx easily and efficiently. Since this are latest version of MySQL and fork mariadb you should do some extra caution during root password reset. Below are the easy steps to reset the root password. If you’re getting below error then it seems root password is not working or something bad happens to MySQL root user : ERROR 1045 (28000): Access denied for user 'root'@'localhost' (using password: YES) Lets get started with MySQL/mariadb root password reset :- First stop the MySQL/Mariadb service : systemctl stop mysqld mariadb mysql service mysqld stop / service mariadb stop Then you need to run the below command to start mysql with skip-grant-tables option : mysqld --skip-grant-tables --user=root & if upper user with root not work you can use below with mysql mysqld --skip-grant-tables --user=mysql & After running the above command press “Enter” Key or "ctrl+c" > to get the shell again Then you need to run mysql command and then run flush privileges command under MySQL CLI: mysql FLUSH PRIVILEGES; Then at last change the MySQL/Mariadb root password : ALTER USER 'root'@'localhost' IDENTIFIED BY 'root_passowrd'; Replace “root_password” with some password. then exit from MySQL cli by typing “quit“ Then run this command to kill all mysql processes : killall -u mysql or pkill -U mysql Ensure by running this command to unset environments if you accidentally set any : systemctl unset-environment MYSQLD_OPTS Now Stop and restart mysql systemctl stop mysql mysqld mariadb && systemctl start mysql mysqld mariadb service mysqld stop && service mysqld restart some time mysql/mariadb process are still running you need to kill them manually you can find the process via top command : top -u mysql if it is running then you need to kill the pid with kill -9 "pid no." and restart mysql/mariadb Thats it you’re done with root password reset for MySQL Check by logging into mysql root. CWP and for other control panels only : On control panel like cwp and other panel having /root/.my.cnf ensure you’ve updated the file with new root password which you changed it via upper command For CWP only update the new password in this files:
-
Useful CSF firewall Commands list for System Admins
CSF (ConfigServer Security & Firewall) is a popular firewall and security tool for Linux servers. CSF is full featured firewall which contains many features and works on Linux out of the box. Its a Stateful Packet Inspection (SPI) firewall, Login/Intrusion Detection and Security application for Linux servers. Here are some common commands that you can use with CSF: Start CSF: To start CSF, use the following command: csf -s you can also use systemctl to restart csf and lfd server systemctl start csf lfd Stop CSF: To stop CSF, use the following command: csf -x you can also use systemctl to restart csf and lfd server systemctl stop csf lfd Restart CSF: To restart CSF, use the following command: csf -r you can also use systemctl to restart csf and lfd server systemctl restart csf lfd Check CSF status: To check the status of CSF, use the following command: csf -status Allow an IP address: To allow an IP address through the firewall, use the following command: csf -a you can add the comment after the ip with space example : Unblock an IP address: To unblock an IP address that has been blocked by CSF, use the following command: csf -dr Block an IP address: To block an IP address, use the following command: csf -d you can add the comment after the ip with space example : View blocked IP addresses: To view a list of blocked IP addresses, use the following command: csf -g to find specific ip in blocked list use below command : Unblock all IP addresses: To unblock all IP addresses that have been blocked by CSF, use the following command: csf -df Check for updates to csf but do not upgrade : csf -c To update CSF : csf -u To Force update : csf -uf Get an IP’s information country of origin & hostname/ptr : csf -i IP usage : Hope this helped and you can add your own commands below in the comment to help others.
-
12 Systemctl commands list for System Admins
systemctl is a command-line tool used to manage and control the systemd system and service manager in various Linux distributions. It enables administrators to manage the OS and control the status of services. Further, systemctl is useful for troubleshooting and basic performance tuning. Here are some Commands which need admin/root privilege service_name is the name of the service you want to perform the action for. Start a service: To start a service, use the following command: systemctl start service_name Stop a service: To stop a service, use the following command: systemctl stop service_name Restart a service: To restart a service, use the following command: systemctl restart service_name Enable a service at boot: To enable a service to start automatically at boot, use the following command: systemctl enable service_name Disable a service at boot: To disable a service from starting automatically at boot, use the following command: systemctl disable service_name Check the status of a service: To check the status of a service, use the following command: systemctl status service_name List all running services: To list all running services, use the following command: systemctl list-units --type=service --state=running example : [root@cwp ~]# systemctl list-units --type=service --state=running UNIT LOAD ACTIVE SUB DESCRIPTION amavisd.service loaded active running Amavis mail content checker atd.service loaded active running Job spooling tools cbpolicyd.service loaded active running CWP Policyd for Postfix clamd.service loaded active running clamd scanner () daemon console-getty.service loaded active running Console Getty crond.service loaded active running Command Scheduler cwp-phpfpm.service loaded active running The PHP FastCGI Process Manager cwpsrv-phpfpm.service loaded active running The PHP FastCGI Process Manager cwpsrv.service loaded active running CentOS Web Panel service (daemon) dbus.service loaded active running D-Bus System Message Bus dovecot.service loaded active running Dovecot IMAP/POP3 email server getty@tty2.service loaded active running Getty on tty2 httpd.service loaded active running Web server Apache lfd.service loaded active running ConfigServer Firewall & Security - lfd mariadb.service loaded active running MariaDB 10.11.2 database server named.service loaded active running Berkeley Internet Name Domain (DNS) nginx.service loaded active running nginx - high performance web server opendkim.service loaded active running DomainKeys Identified Mail (DKIM) Milter php-fpm81.service loaded active running The PHP FastCGI Process Manager php-fpm82.service loaded active running The PHP FastCGI Process Manager postfix.service loaded active running Postfix Mail Transport Agent pure-ftpd.service loaded active running Pure-FTPd FTP server rsyslog.service loaded active running System Logging Service saslauthd.service loaded active running SASL authentication daemon. spamassassin.service loaded active running Spamassassin daemon sshd.service loaded active running OpenSSH server daemon systemd-journald.service loaded active running Journal Service systemd-logind.service loaded active running Login Service systemd-udevd.service loaded active running udev Kernel Device Manager varnish.service loaded active running Varnish Cache, a high-performance HTTP accelerator xinetd.service loaded active running Xinetd A Powerful Replacement For Inetd Find a service name use grep : systemctl list-units --type=service --state=running | grep keyword example : [root@server ~]# systemctl list-units --type=service --state=running | grep php php-fpm81.service loaded active running The PHP FastCGI Process Manager php-fpm82.service loaded active running The PHP FastCGI Process Manager List all failed services: To list all running services, use the following command: systemctl list-units --type=service --state=failed example : [root@cwp ~]# systemctl list-units --type=service --state=failed UNIT LOAD ACTIVE SUB DESCRIPTION * systemd-sysctl.service loaded failed failed Apply Kernel Variables * systemd-vconsole-setup.service loaded failed failed Setup Virtual Console * vzquota.service loaded failed failed LSB: Start vzquota at the end of boot To Stop/masking a service strictly so no one or other programs can start it : systemctl mask service_name To unmasking a service and undo : systemctl unmask service_name Reload systemd configuration: To reload the systemd configuration after changes is done or to just reload it, use the following command: systemctl daemon-reload View service logs: To view the logs of a service, use the following command: journalctl -u service_name example : [root@cwp ~]# journalctl -u httpd -- Logs begin at Wed 2023-05-05 18:48:58 EDT, end at Sat 2023-05-06 15:20:01 EDT. -- Aug 04 04:25:14 cwp.onefinehost.com systemd[1]: Stopping Web server Apache... Aug 04 04:25:14 cwp.onefinehost.com systemd[1]: Stopped Web server Apache. Aug 04 04:25:14 cwp.onefinehost.com systemd[1]: Starting Web server Apache... Aug 04 04:25:14 cwp.onefinehost.com systemd[1]: Started Web server Apache. Aug 04 04:25:14 cwp.onefinehost.com systemd[1]: Reloading Web server Apache. Aug 04 04:25:14 cwp.onefinehost.com systemd[1]: Reloaded Web server Apache. Aug 04 04:25:15 cwp.onefinehost.com systemd[1]: Reloading Web server Apache. Aug 04 04:25:15 cwp.onefinehost.com systemd[1]: Reloaded Web server Apache. Aug 04 04:25:17 cwp.onefinehost.com systemd[1]: Stopping Web server Apache...
-
How to Increase Upload limit for phpMyAdmin, Roundube and File Manager in CWP
great and yes cwp php-fpm uses .user.ini for users, always modify the php values from user panel.
-
How to Increase Upload limit for phpMyAdmin, Roundube and File Manager in CWP
i see the correct php.ini is loaded in your screenshot, normally this type of issue doesn't comes with cwp php versions.
-
How to Increase Upload limit for phpMyAdmin, Roundube and File Manager in CWP
you can PM me with server root details for the checks.
-
How to Increase Upload limit for phpMyAdmin, Roundube and File Manager in CWP
hi run this below command : sh /scripts/php_big_file_upload 128 or sh /scripts/php_big_file_upload 64
-
2FA for CWP
yes in future there will be 2fa for both panels.
-
2FA for CWP
I've identified the issue and the devs are working on it this will be resolved soon in next version of cwp. For CWP-admin 2fa will not be releases as of now but our devs have this in there to do list.
-
Replace rsyslog with Syslog-ng - System Logging Next Generation in CWP, Centos, Almalinux, Rockylinux
In this tutorial we'll learn how you can replace rsyslog with Syslog-ng (System Logging Next Generation) this tutorial will also help if for some reason rsyslog is not working in your server you can relace it with Syslog-ng , it is an open-source, highly configurable, and flexible log management tool. It is used for collecting, processing, and storing log messages from various sources in a centralized location. Syslog-ng is an enhanced replacement for the traditional syslogd service and offers more advanced features and capabilities. Key features of syslog-ng include: Log Collection: Syslog-ng can collect log messages from a wide range of sources, including local log files, remote hosts, network devices, applications, and more. It supports various log message formats, making it versatile for handling different types of logs. Log Routing and Filtering: With syslog-ng, you can define sophisticated log routing and filtering rules based on message content, source, facility, severity, or other criteria. This allows you to route specific logs to different destinations and filter out irrelevant or sensitive information. Log Transformation: Syslog-ng can modify log messages before storing or forwarding them. You can perform tasks like adding or removing fields, enriching log data, or anonymizing sensitive information to comply with data privacy regulations. Reliable Log Transport: Syslog-ng ensures reliable log transport with features like TLS encryption, message acknowledgment, and retransmission mechanisms. This helps prevent log message loss and ensures the integrity and confidentiality of log data during transit. Centralized Log Management: By sending logs to a centralized server, you can easily monitor, search, and analyze log data from multiple sources in one location. This simplifies log analysis and troubleshooting processes. Integration with SIEMs and Big Data Solutions: Syslog-ng can integrate with Security Information and Event Management (SIEM) systems and big data solutions like Elasticsearch, enabling you to leverage advanced analytics and visualization capabilities for log data. High Performance and Scalability: Syslog-ng is designed to handle a large volume of log data efficiently and can scale to meet the needs of enterprise-level environments. Community and Enterprise Editions: Syslog-ng is available in both community and enterprise editions. The community edition is free and open-source, while the enterprise edition provides additional features, support, and commercial licensing options. Step 1 : Remove rsyslog : yum remove rsyslog ** for centos 8 and above you can also use dnf in place of yum Step 2 : Install epel repo and syslog-ng yum install epel-release -y yum install syslog-ng ** for centos 8 and above you can also use dnf in place of yum Step 3 : Enable syslog-ng service and start the service : systemctl enable syslog-ng systemctl start syslog-ng That's it syslog-ng is now enabled and working check the /var/log/messages
-
Disable dangerous PHP functions and improve PHP security - CWP Centos, debian, ubuntu
In this tutorial we'll learn how you can disable dangerous PHP functions. Disabling dangerous PHP functions can help improve the security of your web application by preventing potential exploits and attacks. However, it's important to be cautious when disabling functions, as it may impact the functionality of your application. Only disable functions that are truly unnecessary and represent a significant security risk. Here are some steps you can take to disable dangerous PHP functions: Use PHP Configuration (php.ini): Many PHP functions can be disabled or restricted through the PHP configuration file (php.ini). Access to this file is usually restricted to server administrators, so you may need to contact your hosting provider or server administrator to make changes. Using php.ini or .user.ini : Look or add the disable_functions directive in the php.ini or in .user.ini file and list/add the functions you want to disable, separated by commas. For example: disable_functions = exec,system,passthru,popen,proc_open,shell_exec **you need to restart Apache or php-fpm service after you added this directive. Using .htaccess when using Apache php DSO - mod_php module : Use .htaccess (Apache): If you're using the Apache web server, you can also disable PHP functions via the .htaccess file in your web application's root directory. However, this method requires the "mod_php" module to be enabled, and you should have the necessary permissions to modify .htaccess. Add the following line to your .htaccess file to disable a function: php_flag disable_functions "exec, system, passthru, popen, proc_open, shell_exec" **restart Apache service after you've added this directive. Please note : Regularly update your PHP version and libraries, apply security patches to your CMS/scripts, and follow secure coding practices to build a robust and secure web application
-
How to install Lets Encrypt SSL in Control web Panel - CWP hostname, admin control panel and for Email Server
In this tutorial We'll install Lets Encrypt free SSL in Control web panel, so you can access the admin panel and user panel url in https also for mail server and hostname. Follow the below steps to get ssl installed. Step 1 : Choose a valid Hostname i.e it should be the subdomain of your main domain example : ** ensure whatever you choose as a hostname url you should have valid A record DNS pointing to the server ip *** don't choose mail.domain.tld or cpanel.domain.tld or ftp.domain.tld or webmail.domain.tld as this are reserved for cwp admin services. Step 2 : Change the hostname : Go to CWP-admin >> search >> search for change hostname >> open change hostname module Step 3 : Install Lets encrypt ssl for hostname : By entering the hostname click on "change hostname" button that's it the module will install Lets encrypt ssl automatically for hostname, control panel urls and mail server the hostname module will add ssl to everywhere, now check the admin panel url : https://server1.domain.tld:2031/ and user panel url https://server1.domain.tld:2083 it should be opening with proper ssl certs.
-
How to install Lets Encrypt SSL in Hestia CP hostname, admin control panel and for Email Server
In this tutorial We'll install Lets Encrypt free SSL in Hestia Control panel, so you can access the admin panel in https also for mail server and hostname. The developers built an easy script for it, you need to run the bwlo command to get the ssl installed for hostname, email server and hestia admin panel Step 1 : Choose a valid Hostname i.e it should be the subdomain of your main domain example : server1.domain.tld or alphagnu.domain.tld ** ensure whatever you choose as a hostname url you should have valid A record DNS pointing to the server ip Step 2 : Change the hostname : v-change-sys-hostname server1.domain.tld Step 3 : Install Lets encrypt ssl for hostname : v-add-letsencrypt-host this script will add ssl to everywhere now check the admin panel : https://server1.domain.tld:8083 it should be opening with proper ssl certs.
-
How to install Hestia control panel in Debian 12/11 Ubuntu 22.04
In this tutorial we’ll learn How to install HestiaCP control panel which is similar like vestacp and made by one developer of vesta control panel. Since Vestacp is not updating there features anymore and it seems dead project already I recommend you to move to Hestiacp as soon as possible. They have some extended features in there panel and there forum support is excellent. Make sure that your server is running a supported operating system : Debian 10 Debian 11 Debian 12 Ubuntu 20.04 LTS Ubuntu 22.04 LTS Also ARM server will also work with hestia cp. Our website alphagnu.com also uses ARM server with hestia cp. I recommend to use debian 12 or debian 11 for stable production environment. Homepage : https://hestiacp.com HestiaCP Demo : https://demo.hestiacp.com:8083/ Step 1: Login as root into your server via ssh client like putty or Linux terminal Step 2: Preparing install deps/requirements : apt install sudo wget curl Download Hestiacp install script : wget https://raw.githubusercontent.com/hestiacp/hestiacp/release/install/hst-install.sh Step 3: Run below command according to your software choice : Ensure you change this with your details in below installation flag : **here port 8083 is the admin/user gui port for hestia cp you can chnage the port too by changing the --port 8083 to your fav port number. To install Nginx + Apache + php-fpm with multiphp, email server with clamav and spamassassin and installs mariadb server (requires 2gb ram and above): sudo bash ./hst-install.sh --apache yes --phpfpm yes --multiphp yes --mysql yes --postgresql no --vsftpd yes --proftpd no --exim yes --dovecot yes --clamav yes --spamassassin yes --iptables yes --fail2ban yes --quota yes --api yes --hostname server.domain.tld --email admin@gmail.com --port 8083 --password admin_password --lang en To install Nginx + php-fpm with multiphp, email server with clamav and spamassassin and installs mariadb server (requires 2gb ram and above): sudo bash ./hst-install.sh --apache no --phpfpm yes --multiphp yes --mysql yes --postgresql no --vsftpd yes --proftpd no --exim yes --dovecot yes --clamav yes --spamassassin yes --iptables yes --fail2ban yes --quota yes --api yes --hostname server.domain.tld --email admin@gmail.com --port 8083 --password admin_password --lang en To install Apache + php-fpm with multiphp, email server with clamav and spamassassin and installs mariadb server (requires 2gb ram and above): sudo bash ./hst-install.sh --apache yes --phpfpm yes --multiphp yes --mysql yes --postgresql no --vsftpd yes --proftpd no --exim yes --dovecot yes --clamav yes --spamassassin yes --iptables yes --fail2ban yes --quota yes --api yes --hostname server.domain.tld --email admin@gmail.com --port 8083 --password admin_password --lang en For 1 gb ram and above, if you need only Nginx + Apache + php-fpm with multiphp and light email server without security (clamav and spamassassin) with mariadb : sudo bash ./hst-install.sh --apache yes --phpfpm yes --multiphp yes --mysql yes --postgresql no --vsftpd yes --proftpd no --exim yes --dovecot yes --clamav no --spamassassin no --iptables yes --fail2ban yes --quota yes --api yes --hostname server.domain.tld --email admin@gmail.com --port 8083 --password admin_password --lang en For 1 gb ram and above, if you need only Nginx + php-fpm with multiphp and light email server without security (clamav and spamassassin) with mariadb : sudo bash ./hst-install.sh --apache no --phpfpm yes --multiphp yes --mysql yes --postgresql no --vsftpd yes --proftpd no --exim yes --dovecot yes --clamav no --spamassassin no --iptables yes --fail2ban yes --quota yes --api yes --hostname server.domain.tld --email admin@gmail.com --port 8083 --password admin_password --lang en Suppose you want to install postgresql change the option “–postgresql no” to “–postgresql yes” to disable revert the option yes to no. That's it if you need installation support you can use this forum.
-
How to clear Linux RAM memory cache and free up SWAP memory
IN this tutorial I’ll show you how you can easily clear ram cache and swap memory to speed up the Linux server. You all are familiar with word CACHE which usually represents performance benefits like cache can improve website’s loading speed and similarly cache will improve Linux server performance too in some places. Normally cache are managed by Linux Kernel efficiently and will be cleaned overtime when not in use. Cache cleaning is necessary to refresh and free up the system memory so a new version of cache can be built by eliminating old cache. In result it will help your Server to run even faster with fresh cache. Let’s get started with the tutorial : Please note it is not recommended running Level 3 cache on regular basis, use it when you need to free up memory and cache. It is recommend to use level 1 cache clearing only. Here there are 3 levels of RAM cache clearing commands : vm.drop_caches=1 : This is will clear pagecache – recommended sync; echo 1 > /proc/sys/vm/drop_caches vm.drop_caches=2 : This is will clear dentries and inodes sync; echo 2 > /proc/sys/vm/drop_caches vm.drop_caches=3 : This is will clear pagecache, dentries and inodes i.e. all cache are cleared sync; echo 3 > /proc/sys/vm/drop_caches Clear Swap Memory : Clearing swap memory can take time depending disk speed and the size of the swap memory usage, to clear it simply run this command : swapoff -a && swapon -a ** also don’t use cache clearing command under cron jobs, this commands should be run manually and automation is not recommended.
-
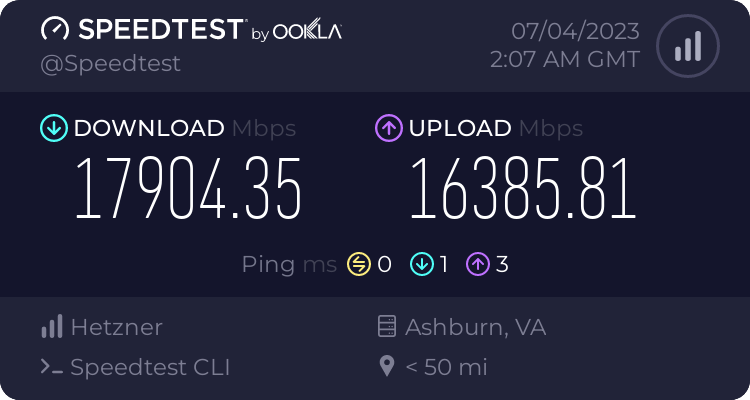
Check Internet Speed of the Server via Linux Command – SpeedTest-CLI
In this tutorial we’ll test and check the server network connection speed via speedtest-cli (Speedtest by Ookla), the best thing is you can directly install the speedtest python package to your Linux distro and run the test via terminal command isn’t is awesome. This will also help you to determine that what exactly network speed your server provider is providing. Without waiting lets get started. Difficulty level : super easy For Centos/EL 7/centos 8 stream/centos 9 stream curl -s https://packagecloud.io/install/repositories/ookla/speedtest-cli/script.rpm.sh | sudo bash yum install speedtest to run the speedtest type below command : speedtest **accept the license by typing "yes" For Ubuntu/Debian : sudo apt-get install curl curl -s https://packagecloud.io/install/repositories/ookla/speedtest-cli/script.deb.sh | sudo bash sudo apt-get install speedtest to run the speedtest type below command : speedtest **accept the license by typing "yes" For other OS : mkdir -p /usr/local/ookla cd /usr/local/ookla wget https://install.speedtest.net/app/cli/ookla-speedtest-1.2.0-linux-x86_64.tgz tar zxvf ookla-speedtest-1.2.0-linux-x86_64.tgz to run the speedtest type below command : cd /usr/local/ookla ./speedtest **accept the license by typing "yes" it will show the speed results like below : Speedtest by Ookla Server: Frontier - Ashburn, VA (id: 14229) ISP: Hetzner Online GmbH Idle Latency: 0.32 ms (jitter: 0.00ms, low: 0.31ms, high: 0.32ms) Download: 17904.35 Mbps (data used: 9.7 GB) 1.25 ms (jitter: 0.27ms, low: 0.34ms, high: 1.86ms) Upload: 16385.81 Mbps (data used: 15.5 GB) 2.86 ms (jitter: 0.79ms, low: 0.68ms, high: 7.50ms) Packet Loss: 0.0% Result URL: https://www.speedtest.net/result/c/524965dc-5310-4b38-9ce6-218bf4de7d0b